Smart cities applications’ security and trust through edge computing virtualization: the 5GCity approach
www.virtualopensystems.com/en/products/vosystrustedvim/
Security and trust are essential in smart cities environments because of the importance of the data they process and for their distributed architecture. In fact, citizen’s data coming from cameras, smart devices, mobility services, etc. need to be protected from data leakages, attacks and retaliations. Moreover, in 5G environments where edge devices are scattered throughout the city and eventually connected through wireless technologies, the risk of man-in-the-middle and denial of service attacks is significant. To make things worse, edge devices are often placed in positions difficult to secure, and it might be relatively easy for an attacker to modify, replace or tamper them.
As a result, smart cities infrastructure security and trustworthiness are key challenges to be solved to fully implement the concept of city of the future.
To respond to these challenges, 5GCity includes a virtualization-based security and trust infrastructure for Arm edge devices. It can be used by smart city applications developers to enhance security, authenticate devices and secure citizens’ data. This infrastructure includes VNFs, NFVI and VIM extensions, leveraging the root of trust capabilities of the hardware and providing security and trust features at the lower level of the software architecture.
The security and trust extensions that will empower the 5GCity EdgeNFVI and EdgeVIM are built upon Virtual Open Systems’ technology VOSYSmonitor, a certified high performance and low latency monitor layer for mixed-criticality systems.
In the next sections, these security and trust extensions will be explained in more detail, starting from the part related to the NFVI and VNFs (Edge NFVI), before detailing the VIM enhancements (EdgeVIM).
EdgeNFVI: NFVI and VNFs TPM extensions
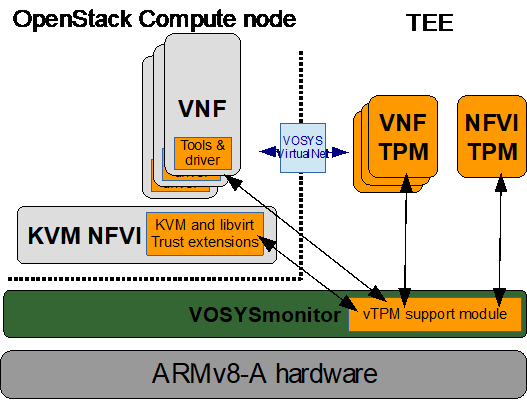
As previously mentioned, key pillar of the 5GCity security and trust extensions for NFVI and VNFs is VOSYSmonitor, a system partitioner for Arm devices that leverages Arm TrustZone to enable Trusted Execution Environment (TEE), i.e., a secure area of the main processor that provides an isolated and trusted environment.
This TEE is used for the implementation of a virtualized
Trusted Platform Module (TPM), a set of security features standardized by the Trusted Computing Group. The virtualized TPMs functions are made available to the VNFs and to the hypervisor.
- VNFs: vTPMs are used to enhance the security of the networking functions with secret storage and cryptographic functions. A standardized library will be used in the VNFs to get security functions, providing applications portability.
- Hypervisor: the TPM functions are exposed to the VIM (i.e., secret storage, asset tagging, geo tagging, etc.) and enable VNF attestation and secure boot.
EdgeVIM: bringing trust at the VIM level
5GCity’s EdgeVIM is based on OpenStack and leverages EdgeNFVI (running on Arm TrustZone enabled devices) to provide security/trust SLAs and services, supporting multitenancy and targeting neutral host scenarios. As shown in the below picture, specific attestation agent and service applications are deployed in the controller and compute nodes to support remote attestation, geo-fencing and asset tagging. Additionally, a purpose-built Nova filter is developed to attest the identity and the security features of each compute node before the deployment of new VMs.
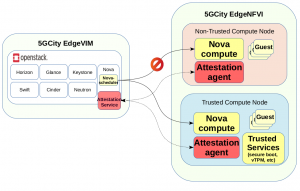
These functions are very important for a number of 5G use cases and verticals. For instance, in the case of the neutral host scenario, for some applications (hospital, banks, local police, etc.) it is very important to ensure that citizens data is processed only in compute nodes trusted from the viewpoints of the hardware and software configuration, device owner, geographic position, etc. Similarly, there are mission critical 5G use cases such as automotive, Industrial IoT, and Mission Critical Communication (MCC) where security flaws put at risk the life of the smart city citizens. In this case TPM features are important to strengthen security and avoid failures.



